LTP
LTP is an open source project used for testing a linux kernel. The test suites can be written in c, shell or perl. In this post, I will try to explain my understanding of LTP and a sample test case that I will write and execute using LTP.
Download the source from
http://sourceforge.net/projects/ltp/files/LTP%20Source/ltp-20130904/
Upon going to the parent directory of this, You can find out more recen sources of LTP. As of now the above link is the latest suite.
WHAT LTP CONTAINS
There are test cases inside LTP and a test driver called as "pan".
Once the source is extracted, LTP can be viewed as follows.
SCRIPTS
a) IDcheck.sh -> Creates the groups and users required for running LTP
b) runltp -> main script that is used for executing LTP. It has ability to execute tests related to Sub systems of linux kernel, commands, system calls.
c) Networktest.sh -> To verify features related to network
d) diskio.sh -> verifies disk IO related tests.
DIRECTORIES
a) scenario_groups ->has files which has groups of SCENARIOS to be tested like fs, mm, io, commands, syscalls etc.
b) runtest -> For each scenario described in scenario_groups, these is a corresponding file inside runtest directory which has the Test cases. The format of this file is <TEST CASE TAG> <TEST EXECUTABLE NAME> <Arguments if any>
c) testcases/bin -> This directory consists of each <TEST EXECUTABLE> defined in previous point.
d) testscripts -> contains the scripts that can be used for usage of runltp. Eg : ltpstress.sh etc.
COMPILE AND INSTALL LTP
Once the source is downloaded, perform the following.
1. untar
2. ./configure
3. make
4. sudo make install (will be installed in /opt/ltp)
EXECUTING DEFAULT TEST CASES
1. cd /opt/ltp
2. ./IDcheck.sh
3. sudo ./runltp -p -o output.log -f commands
Point 3 illustrates a sample execution of a particular sub sytem/feature in LTP.
WRITING CUSTOM TEST CASE AND EXECUTION
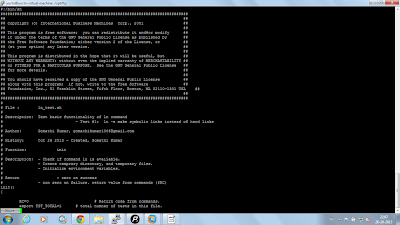
This is a sample program.
The customized test script can be added in /opt/ltp/testcases/bin/ folder
To execute this script it has to be added in one of the run test files Eg : runtest/commands and the format of this file is
Then this runtest can be executed using
sudo ./runltp -p -o output.log -f commands
The output will be as shown below
and the output log will be of the following format
In Similar way .c file also can be compiled, added and executed.
Thanks,
Gomathi
LTP is an open source project used for testing a linux kernel. The test suites can be written in c, shell or perl. In this post, I will try to explain my understanding of LTP and a sample test case that I will write and execute using LTP.
Download the source from
http://sourceforge.net/projects/ltp/files/LTP%20Source/ltp-20130904/
Upon going to the parent directory of this, You can find out more recen sources of LTP. As of now the above link is the latest suite.
WHAT LTP CONTAINS
There are test cases inside LTP and a test driver called as "pan".
Once the source is extracted, LTP can be viewed as follows.
SCRIPTS
a) IDcheck.sh -> Creates the groups and users required for running LTP
b) runltp -> main script that is used for executing LTP. It has ability to execute tests related to Sub systems of linux kernel, commands, system calls.
c) Networktest.sh -> To verify features related to network
d) diskio.sh -> verifies disk IO related tests.
DIRECTORIES
a) scenario_groups ->has files which has groups of SCENARIOS to be tested like fs, mm, io, commands, syscalls etc.
b) runtest -> For each scenario described in scenario_groups, these is a corresponding file inside runtest directory which has the Test cases. The format of this file is <TEST CASE TAG> <TEST EXECUTABLE NAME> <Arguments if any>
c) testcases/bin -> This directory consists of each <TEST EXECUTABLE> defined in previous point.
d) testscripts -> contains the scripts that can be used for usage of runltp. Eg : ltpstress.sh etc.
COMPILE AND INSTALL LTP
Once the source is downloaded, perform the following.
1. untar
2. ./configure
3. make
4. sudo make install (will be installed in /opt/ltp)
EXECUTING DEFAULT TEST CASES
1. cd /opt/ltp
2. ./IDcheck.sh
3. sudo ./runltp -p -o output.log -f commands
Point 3 illustrates a sample execution of a particular sub sytem/feature in LTP.
WRITING CUSTOM TEST CASE AND EXECUTION
This is a sample program.
The customized test script can be added in /opt/ltp/testcases/bin/ folder
To execute this script it has to be added in one of the run test files Eg : runtest/commands and the format of this file is
Then this runtest can be executed using
sudo ./runltp -p -o output.log -f commands
The output will be as shown below
and the output log will be of the following format
In Similar way .c file also can be compiled, added and executed.
Thanks,
Gomathi