Yippee!! I deployed my virtual machine with android.
It might sound "What is there in it?" But this is my first time I tried it and it was successful. I would like to summarize it here for all those first-handers wondering how to do the same.
1. The first and foremost thing needed to deploy you need the iso. It is mostly observed that android-x86-4.0-RC2-eeepc.iso is well suited for vmware and 4.2 is well suited for virtualbox. The iso can be downloaded from
http://www.android-x86.org/download
In this post I will be covering in detail installation in vmware (and hence 4.0). The iso is a 179Mb file.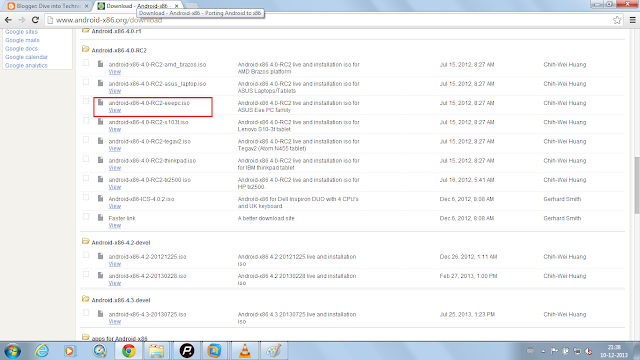
It might sound "What is there in it?" But this is my first time I tried it and it was successful. I would like to summarize it here for all those first-handers wondering how to do the same.
1. The first and foremost thing needed to deploy you need the iso. It is mostly observed that android-x86-4.0-RC2-eeepc.iso is well suited for vmware and 4.2 is well suited for virtualbox. The iso can be downloaded from
http://www.android-x86.org/download
In this post I will be covering in detail installation in vmware (and hence 4.0). The iso is a 179Mb file.

2. Once the iso is downloaded, the vm can be created. Start vmware and perform the following.
b) Select Typical configuration, which is enabled by default.
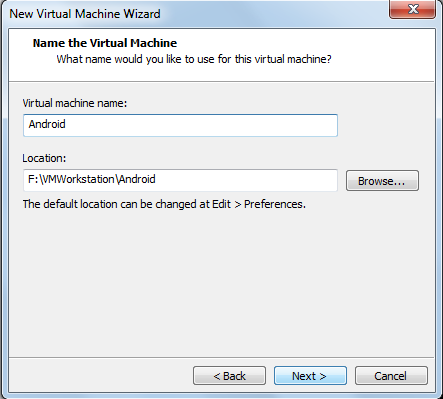
d) Give the name of the virtual machine and path.
e) Give the Maximum disk size.
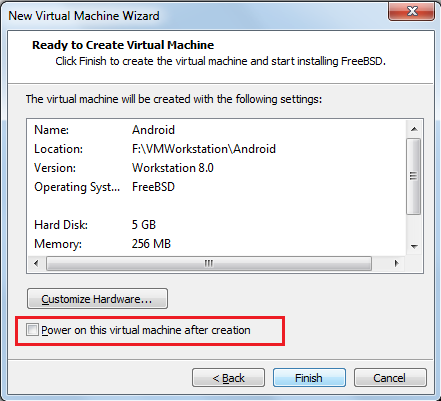
And click finish. The vm will be created.
g) once this is done, go back to the path that was set in point (d). There will be virtual machine configuration file (vmx file)
Open this file with notead.
There will be an entity, ethernet0.virtualDev = "e1000"
Change this to ethernet0.virtualDev = "vlance"
save this file.
h) Go back to vm and power it on.
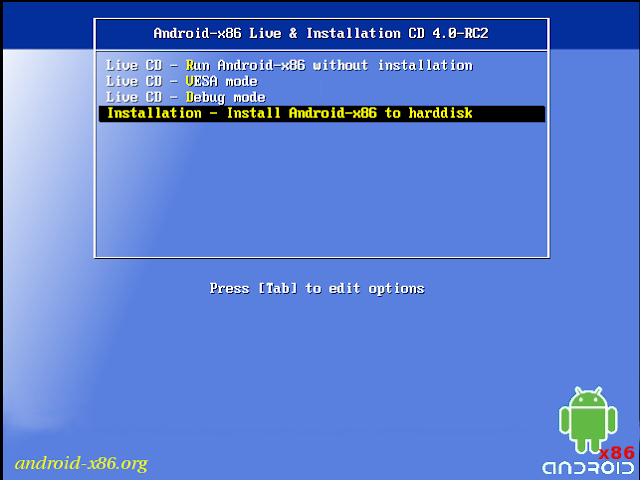
i) Select Install android-x86 to hard disk
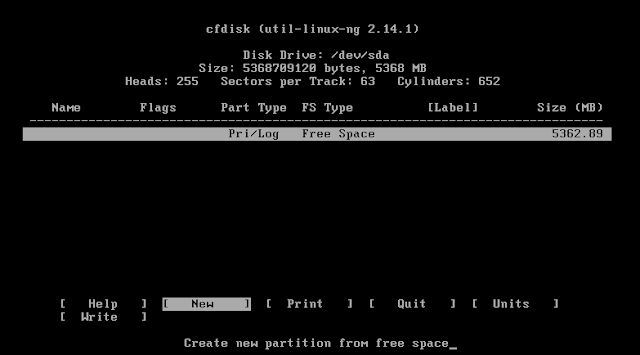
k) This will open a cfdisk utility
Select New
Then select "write"
Select "Quit"to come back to ""Choose partition"window as shown in point (j). The only difference will now be that the partition you added will now be available in that window.
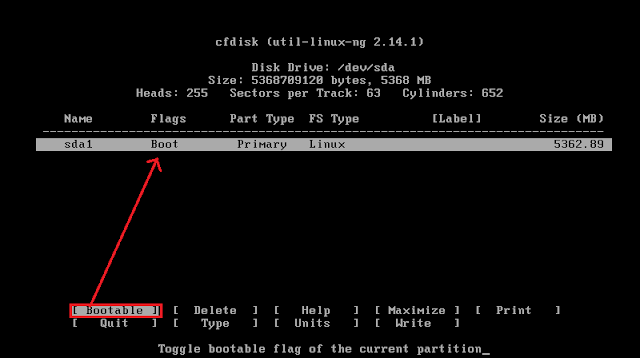
l) Format the partition with ext3 file system.
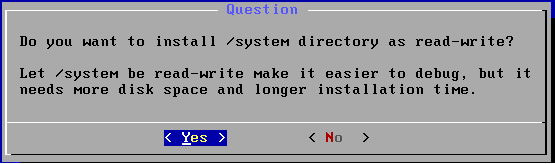
There will be questions like "Do you want to format?"etc. Please select yes.
For setting read/write permission, select yes.
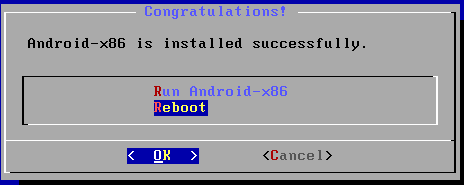
m) After this, select reboot in below screen.
This finishes deployment.
But for usage, some more customization are to be done, which are listed below.
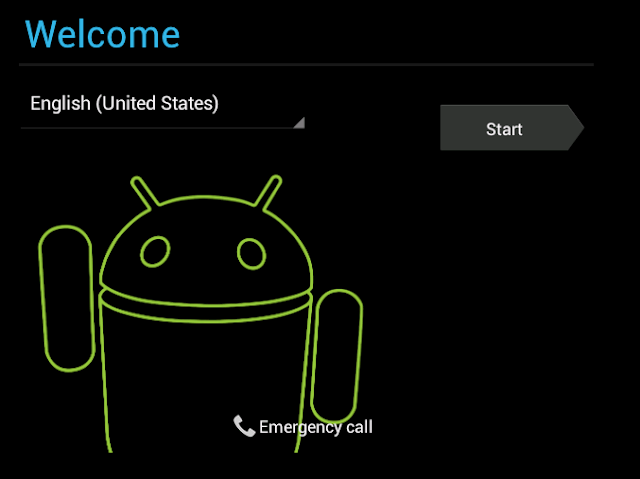
Click on "Start"
b) Press "Next"for the date and time setup.
c) Make sure you do not sign in to google account as yet.
d) Give a name to the owner of the tablet and click next
e) Agree to the google terms and services and click next
f) Click finish
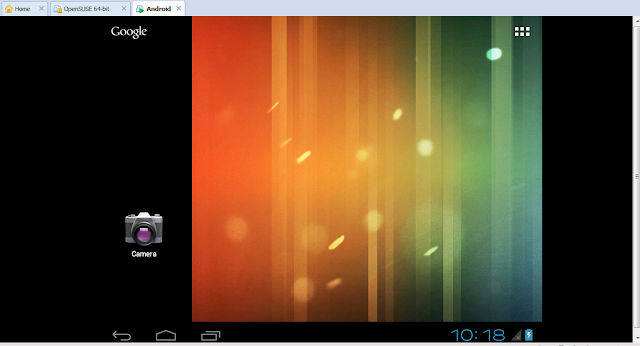
Your vm is up and ready with android.
Network Setup:
1. Open terminal emulator
2. Do su and give root access to terminal emulator.
3. Open /etc/init.sh file and append the following line
setprop net.dns1 8.8.8.8
4. Reboot the machine.
Now your android on VM is set and you can even access web pages.
Hope this was useful.
Thanks,
Gomathi